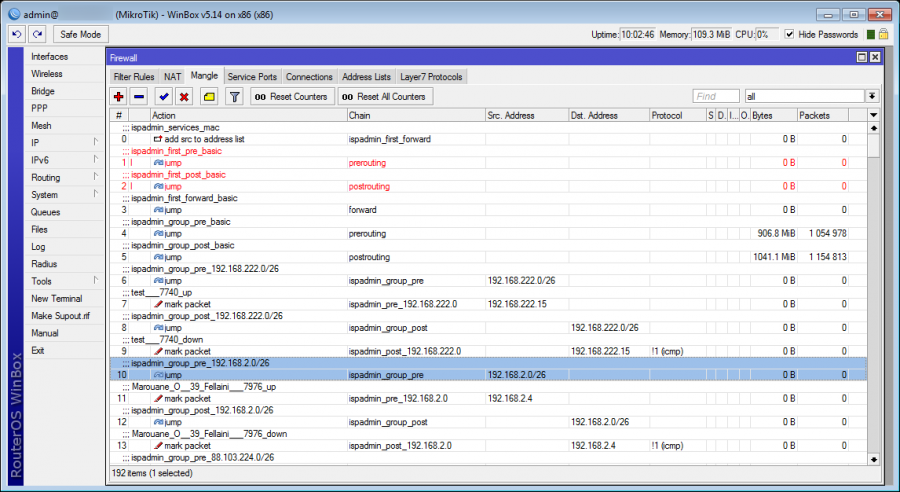
In some cases it is necessary to assign clients into a special QT, e.g. to divide traffic on a router into three groups, where each group represents one connection, for instance into another village. Each connection has its own defined capacity (e.g. 2Mbit).
In this case it is necessary to create a special QT on Mikrotik for each group and define appropriate speed, or set other parameters of this QT manually, because every provider has different requirements, or it is necessary to create more deeply nested structures of the QT, which it is not possible to create automatically.
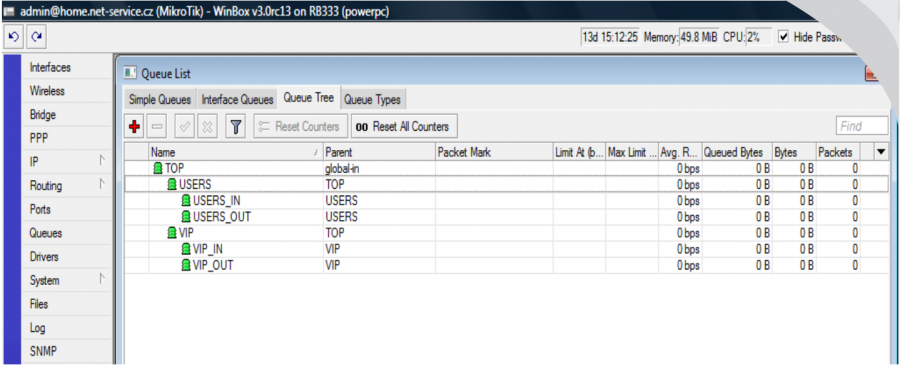
It is necessary to create named QT (which will be entered into the system) on Mikrotik. If the QT is called e.g. VIP, it is necessary to create the following on MK:
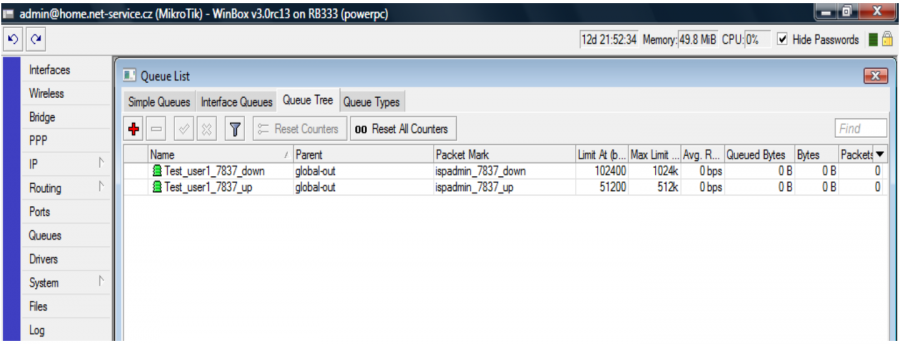
VIP – clients with HD tariff will be assigned to this QT (upload and download are shared)
VIP_IN – download of clients with FD tariff is assigned to this QT
VIP_OUT – upload of clients with FD tariff is assigned to this QT
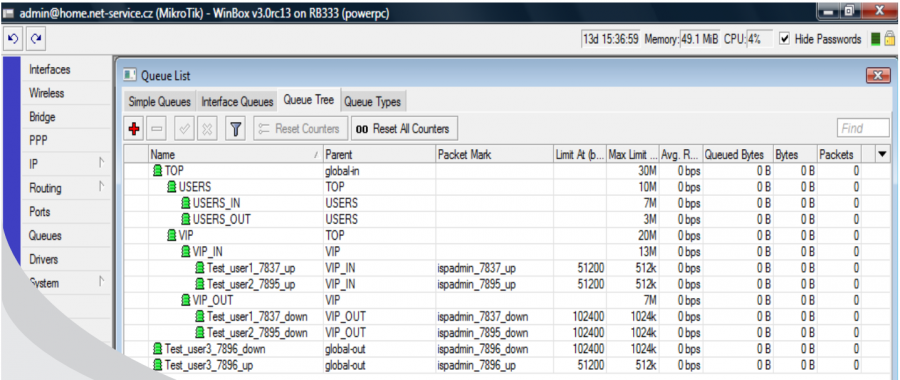
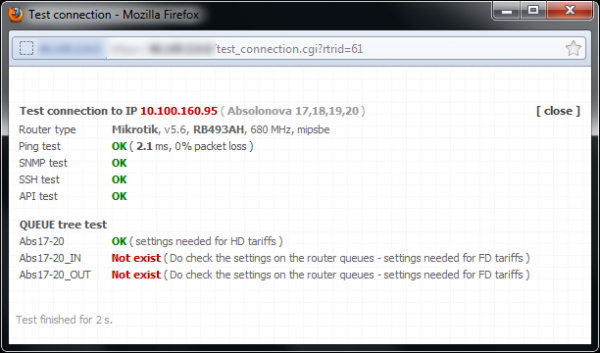
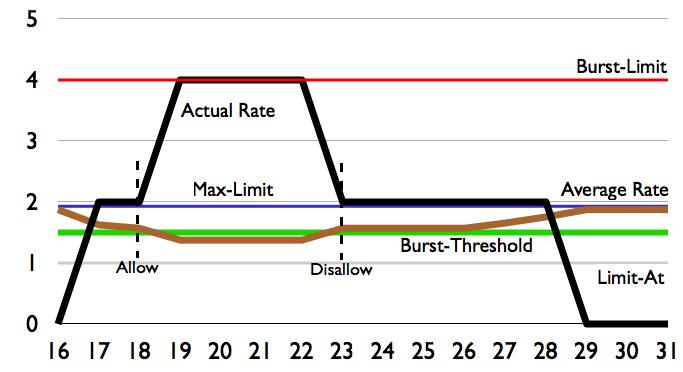
There are 2 client groups - USERS and VIP - created on the example figure above. Speed parameters are defined for each group accordingly; total group speed and download/upload speed are set, it is also possible to allocate here additional restrictions, such as the restriction of P2P nets, or connection totals...
You can adjust the entire tree according to your needs. The system is "interested" only in the "end branches" of the whole tree, where the clients will be assigned. In our VIP example, it is VIP, VIP_IN and VIP_OUT. It does not matter at which level the end "branch" of the tree is located.
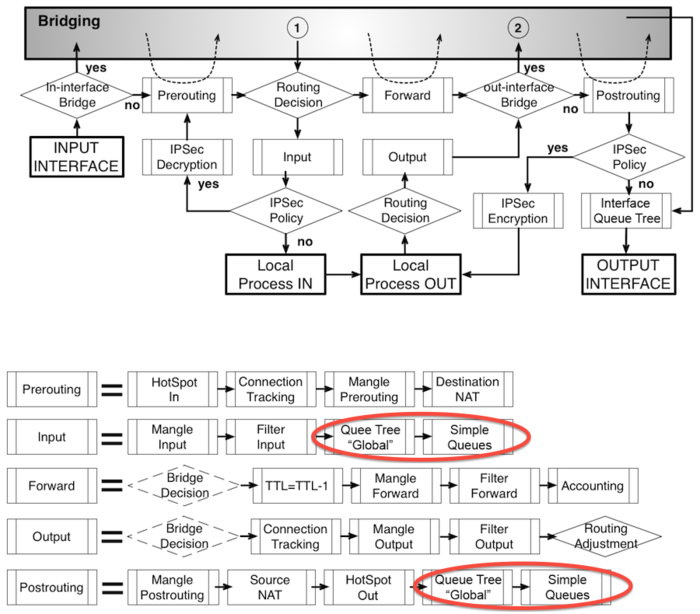
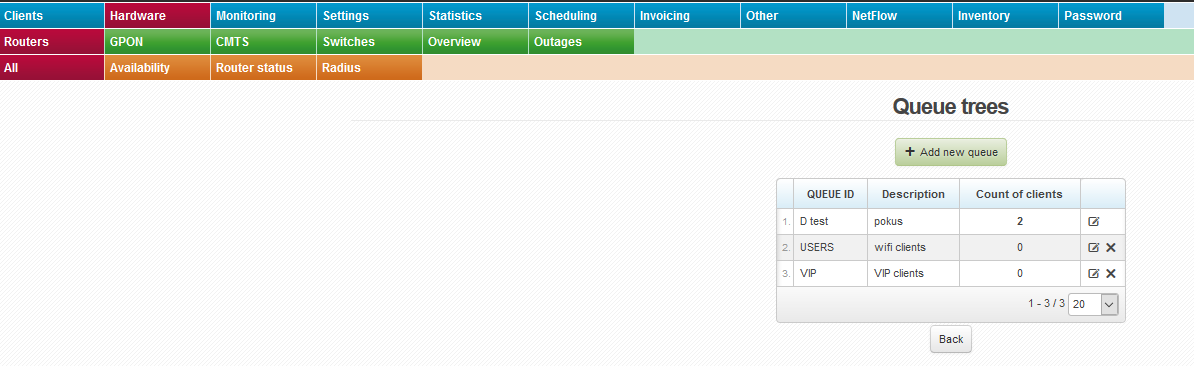
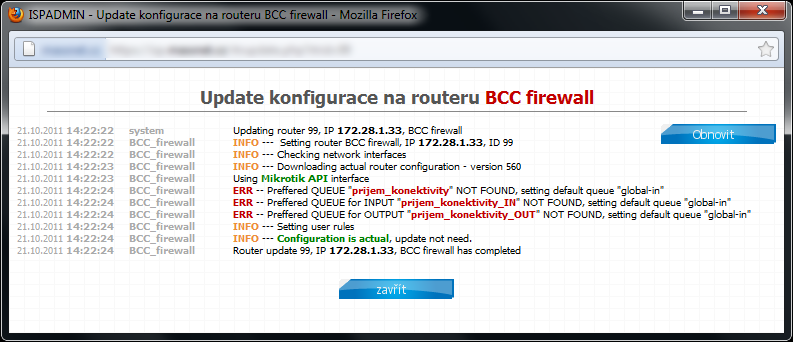
Now you have let ISPadmin know that there is the special QT VIP. To do so, enter it to Queue tree in router heading (Routery). Enter special QT “VIP” here. You do not have to enter QT VIP_IN and VIP_OUT. The existence of these QT is assumed while entering QT VIP. If QT VIP_IN and VIP_OUT are not present in MK (syntax is important; you have to use the same name as in ISPadmin and Mikrotik, plus add suffix _IN and _OUT in capital letters), so the clients with FD tariff will be assigned to QT “global-out” (only “global” for ROS > 6.x) outside this “tree”.
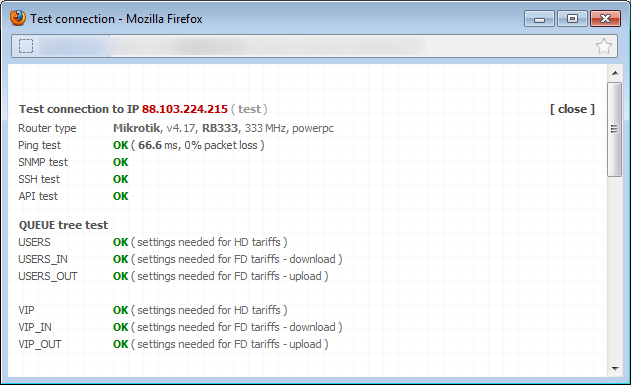
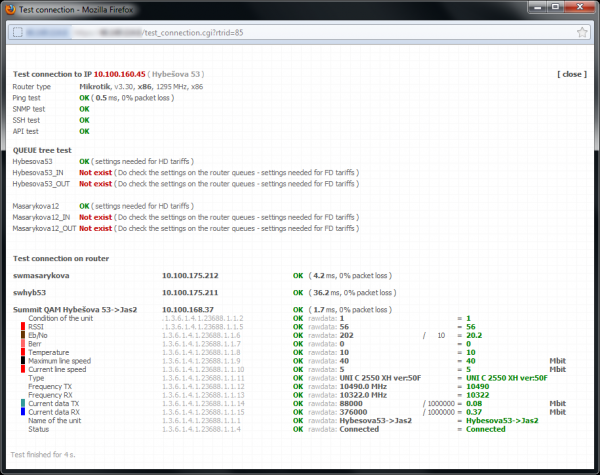
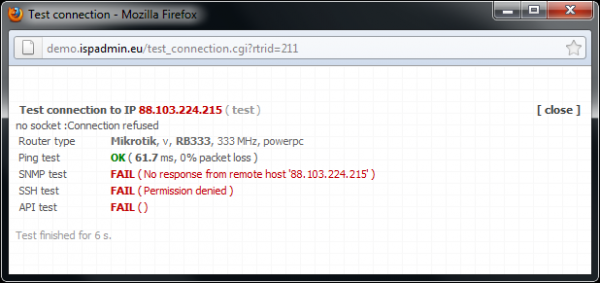
Click on Test connection to test special Queue tree; the test should run flawlessly.
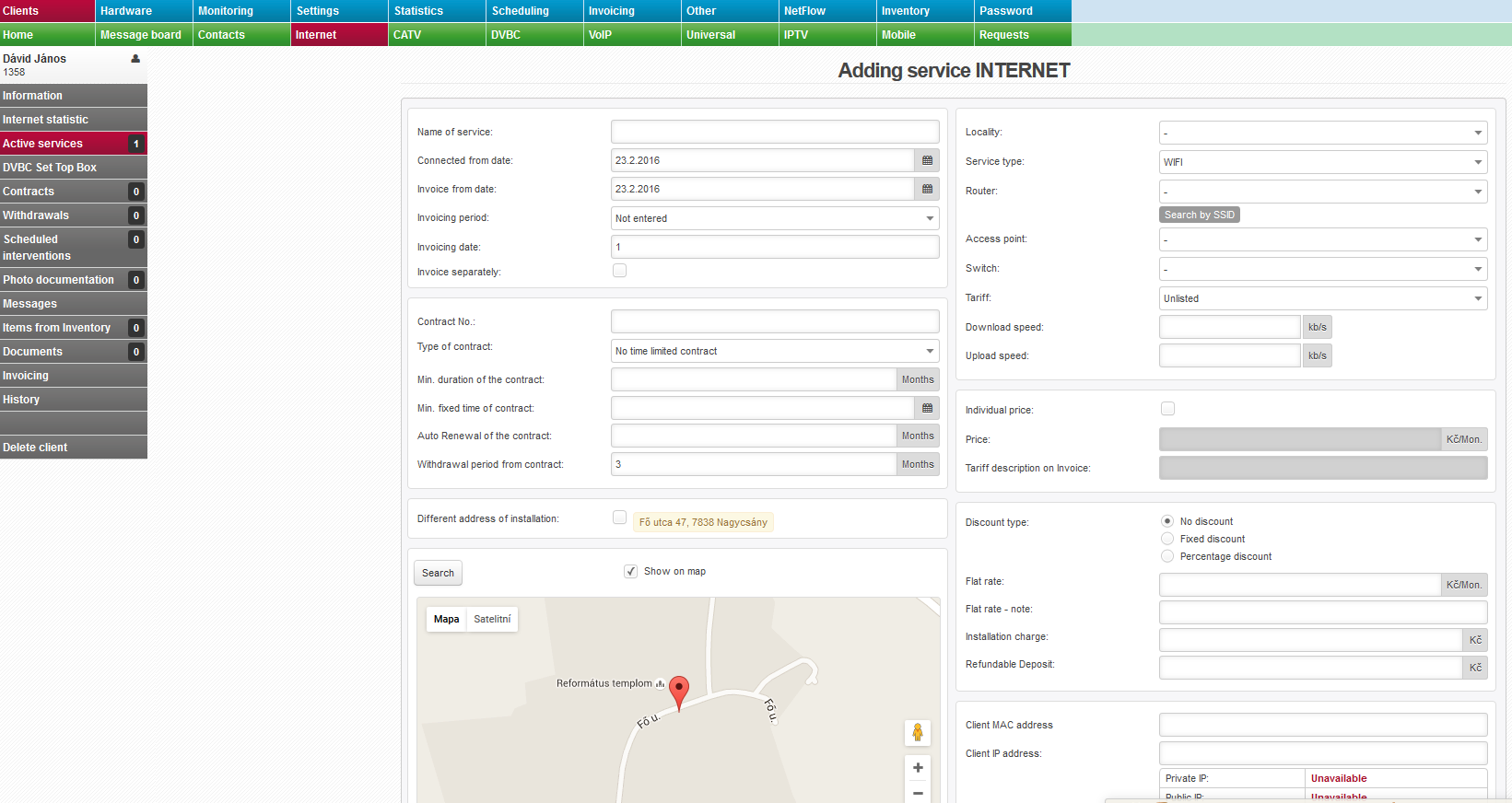
If QT are defined correctly on router and the test runs OK, you can assign client to this special QT. You can do so while adding/editing Internet service in Client card. Select a tariff, a pop-up QT menu appears (if the aggregation is 1:1) where you select QT to which a client is assigned. QT can be selected only if 1:1 aggregation is used. Otherwise QT selection is not displayed. The reason is that if client is assigned to aggregated (shared) tariff you cannot assign him to a special QT since client cannot belong to both, aggregated line and special QT at the same time. Technically, it is not possible to mangle client package twice. A packet can have only one packet mark and so it can logically belong only into one line (aggregated or shared).
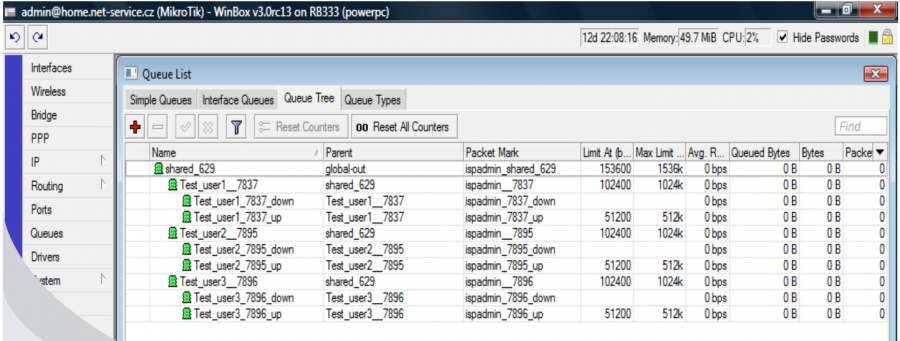
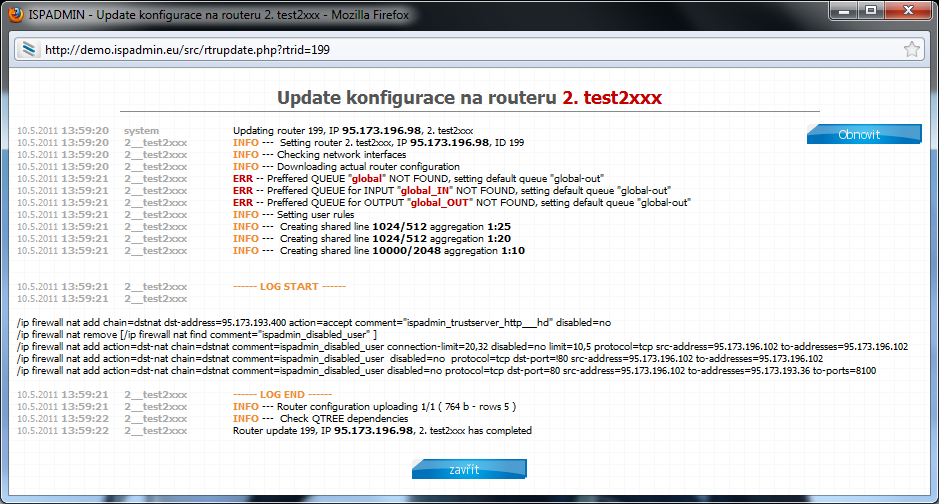
So if you assign client Test_user1 to QT VIP it will be classified in Mikrotik as follows:
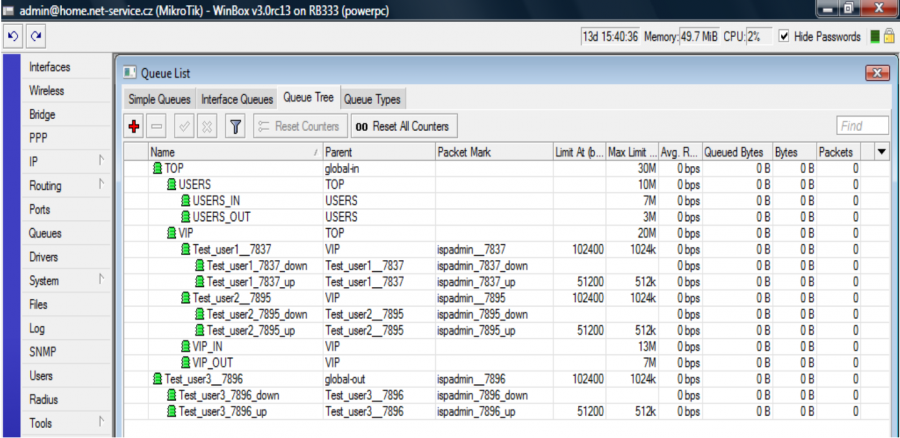
All clients have tariff 1024/512 with aggregation 1:1 and it is a HD tariff. Clients Test_user1 and Test_user2 are assigned to QT VIP. Client test_user3 is normally assigned to "global-out", because he has no QT set. Since it is a FD tariff, clients´ download and upload will be divided into VIP_IN and VIP_OUT .
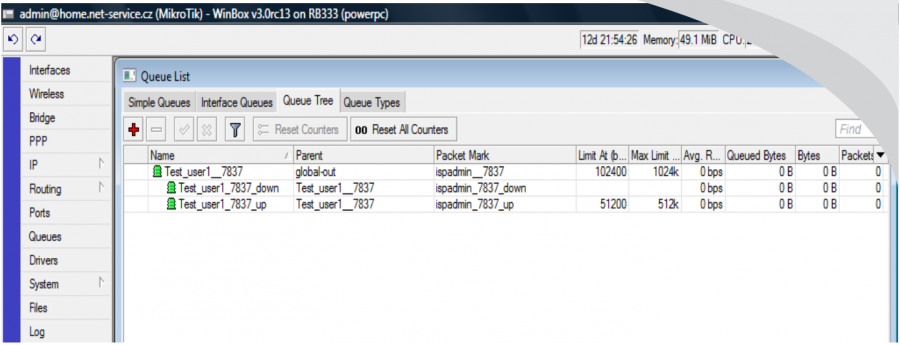
If it is HD tariff, then the clients will be classified as follows:
Clients Test_user1 and Test_user2 are assigned to QT VIP and not in VIP_IN and VIP_OUT as for HD tariff. All clients have a usual HD tariff where download/upload are limited on superior QT, e.g. Test_user1__7837. Client Test_user3 is assigned to "global-out".
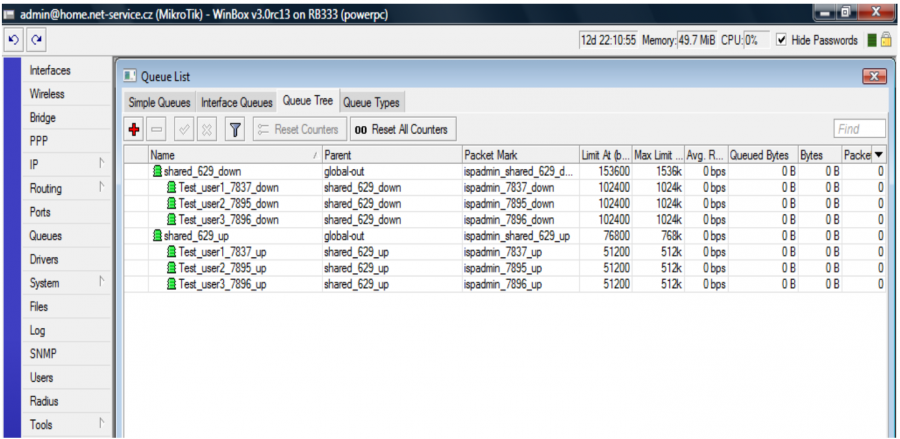
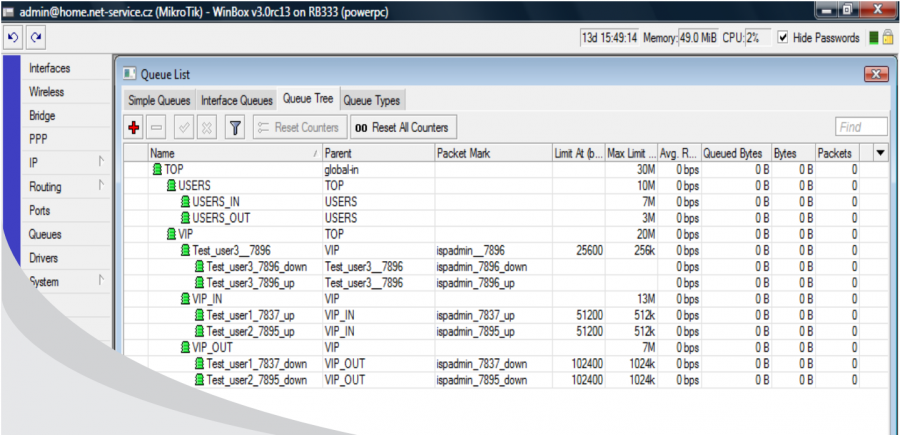
You can combine the above-mentioned procedures as needed. In our example, clients Test_user1 and Test_user2 have FD tariff with 1:1 aggregation and speed 1024/512. Client Test_user3 has HD tariff 256/256, therefore he is assigned to QT VIP.
mikrotik_preffered_queue - All clients must be assigned to a certain QT in some cases. E.g. in case we need to precisely set the overall speed of the line. You can set it according to the previous method, by assigning each client into a particular QT. However, this method is quite tedious and prone to mistakes by not adding a client into a QT and so he will automatically be assigned to global-out. This is why you can define QT to which clients are automatically assigned in case they are not explicitly assigned in another QT ( , ID mikrotik_preffered_queue.) Again, if you set mikrotik_preffered_queue "VIP", then there must be created QT VIP, VIP_IN, and VIP_OUT on a router. The default value of ID mikrotik_preffered_queue is global-out.