Clients
-
You can now add a note to an IPTV service.
-
HU localization: Wrong prices for Internet services were displayed in the Client card, in and in the tariff settings when a special VAT rate for Internet services was used. The bug is fixed now.
-
The form used for adding a new General service to the system has been fixed. Before the fix, it was not possible to enter a price in the form of a decimal number.
- When a credit note is issued, the system, by default, confirms it immediately (the Confirm credit note now checkbox). The note is thus immediately included in the various accounting overviews in the system.
ADMINISTRATOR RIGHTS
- New rights to have been implemented. Previously, the rights were set for MasterAdmin, and for Main admin in some cases. Currently, the rights are automatically set for MasterAdmin only, and you have to set up the rest manually.
Modified script
When running
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl
with check, checkdevices, checkusers, or cleaninfected parameter, a dialog will be displayed, and you will be able to specify the following parameters:
| IP addresses (all) ? : |
You may insert a list of IP addresses to be scanned by typing them. If you leave it blank, the script will use IP addresses from the database. |
| SSH PORT (22) ? : |
Default port for ssh is 22. If your ssh is somewhere else, enter ssh port number here. |
| SSH usernames for connect ( ubnt, admin, mother) ? : |
Usernames used for accessing the units. If blank, the script will try to use ubnt, admin, mother. |
| DEBUG (yes) ? : |
If you select yes, the progress of the test will be displayed in the console. |
Help
Check devices from ISP admin bookmark ROUTERS
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl check - show ONLY vulnerable and infected ROUTERS ( AP )
Check devices like AP ....( may take a long time )
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl checkdevices - show ONLY vulnerable and infected devices ( Acces points )
Check END USER devices ....( may take along time )
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl checkusers - show ONLY vulnerable and infected client end device
Clean INFECTED devices ( from previous check )
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl cleaninfected - show vulnerable and infected devices and REMOVE infection
More on Ubiquiti - security bug in changelog version 4.21, beta1.
Detecting and removing

Reacting to the revealed vulnerability, we released ISPadmin, version 4.20, which included a utility for detecting and curing infected Ubiquiti units. Due to the emergency situation we released the very first version of the utility quickly.
Now we are presenting the utility with enhanced functionalities.
 Run the utility from ISPadmin console (connected via SSH) under root user, ISPadmin does not detect anything automatically!
Run the utility from ISPadmin console (connected via SSH) under root user, ISPadmin does not detect anything automatically!
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl
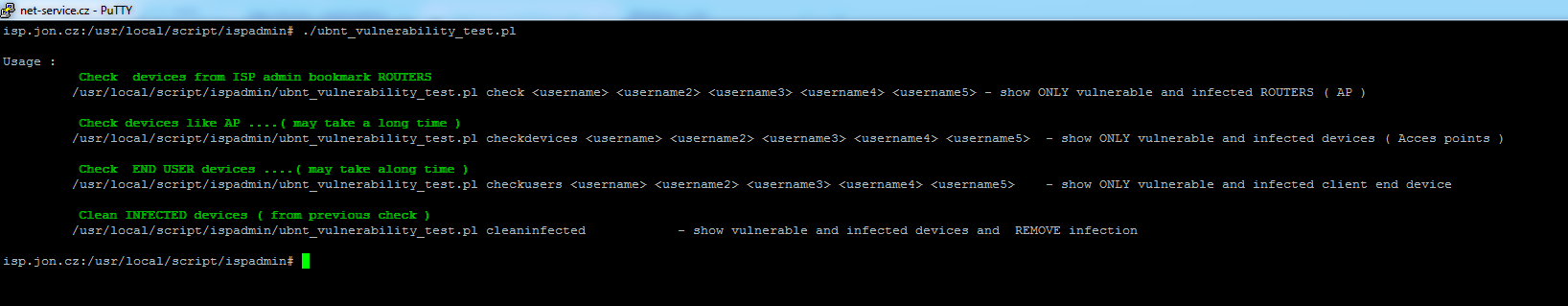
When running the utility without any parameter, help is displayed.
Check devices from ISP admin bookmark ROUTERS
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl check <username> <username2> <username3> <username4> <username5> - show ONLY vulnerable and infected ROUTERS ( AP )
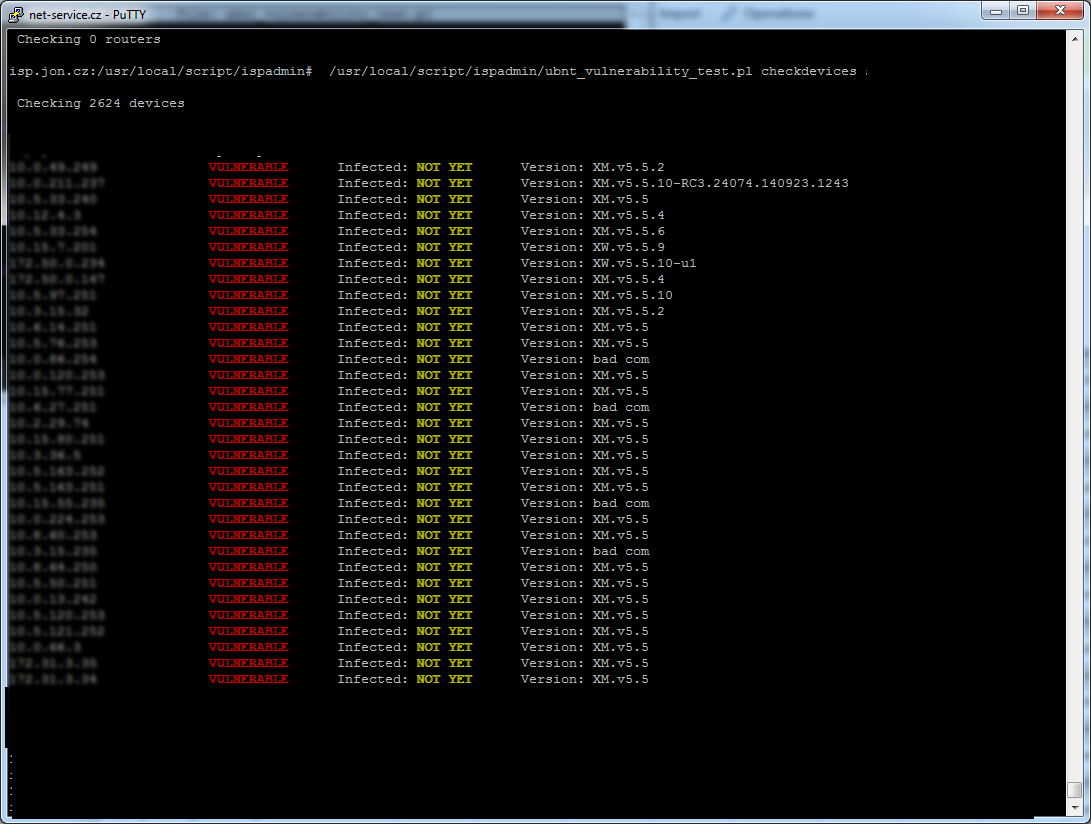
Tests all Ubiquiti units inserted in . If you run this command, the system tries to attack the unit, and if it succeeds, the console displays information with IP address and firmware version. If the system succeeds in connecting to Ubiquiti unit, it tries to determine whether there is the virus or not. If yes, it displays such information in the console. Nothing else. When 10 units are tested, a dot appears on the screen to show you that the script is still running and testing other units.
Check devices like AP ....( may take a long time )
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl checkdevices <username> <username2> <username3> <username4> <username5>
- show ONLY vulnerable and infected devices ( Acces points )
Tests all devices inserted as “Device attached to device” in . In this case, the utility doesn´t care about device type since such information might not be available here. The utility tries to attack all IP addresses. If there are a lot of devices in your system, this might take a long time.
Check END USER devices ....( may take a long time )
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl checkusers <username> <username2> <username3> <username4> <username5>
- show ONLY vulnerable and infected client end device
Tests all IP addresses assigned to clients. The system tests all client-assigned IP addresses for it does not know whether a client has Ubiquiti device, or not. This operation might take a long time, since all IP addresses in the system are tested.
Clean INFECTED devices ( from previous check )
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl cleaninfected
- show vulnerable and infected devices and REMOVE infection
If an infected unit is detected in the previous step, you may clean it this way. This operation connects to and cleans just those units, which are marked as infected. It means that prior to this step you have to run the utility with parameters check, checkdevices, or checkusers. Failing this no units are marked as infected and using parameter “cleaninfected” makes no difference.
A mandatory parameters are: check, checkdevices, checkusers, or cleaninfected. You may use user names, which you use for login to Ubiquiti units as an optional parameter. This is needed in cases when a key is stored in Ubiquiti unit after being attacked to enable login via ssh without password. You need to know the user name with which you connect to the system. If unknown, you won´t be able to connect. While running the vulnerability test, a default user name ubnt and user admin are tested. If you use neither of these, the script won´t be able to test vulnerability hence the need for entering a different username used for accessing the unit (no need for password). Then the system will try using these usernames.
Listing of UBNT units in ISPadmin
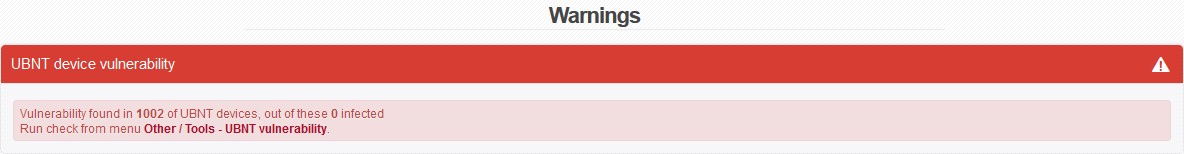
When you log into ISPadmin, you will see information about Vulnerability of UBNT devices:
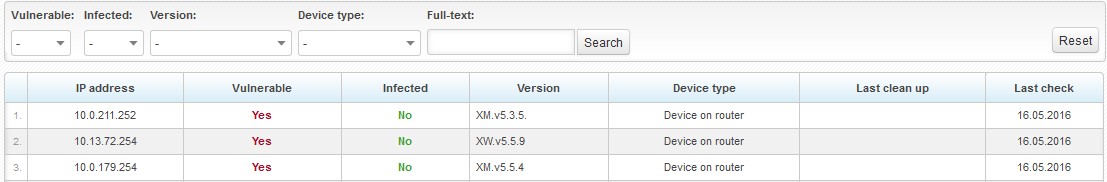
In > Vulnerability of UBNT devices, you will find a tool for displaying vulnerable devices as detected by the utility - see above.
 Check the box at the end of each row (or check all, or you may use reversed selection) to select those devices, for which you want the system to update firmware - by clicking on on the bottom.
Check the box at the end of each row (or check all, or you may use reversed selection) to select those devices, for which you want the system to update firmware - by clicking on on the bottom.
UBIQUITI BUG - MODIFICATION
Modified script
When running
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl
with check, checkdevices, checkusers, or cleaninfected parameter, a dialog will be displayed, and you will be able to specify the following parameters:
| IP addresses (all) ? : |
You may insert a list of IP addresses to be scanned by typing them. If you leave it blank, the script will use IP addresses from the database. |
| SSH PORT (22) ? : |
Default port for ssh is 22. If your ssh is somewhere else, enter ssh port number here. |
| SSH usernames for connect ( ubnt, admin, mother) ? : |
Usernames used for accessing the units. If blank, the script will try to use ubnt, admin, mother. |
| DEBUG (yes) ? : |
If you select yes, the progress of the test will be displayed in the console. |
Help
Check devices from ISP admin bookmark ROUTERS
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl check - show ONLY vulnerable and infected ROUTERS ( AP )
Check devices like AP ....( may take a long time )
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl checkdevices - show ONLY vulnerable and infected devices ( Acces points )
Check END USER devices ....( may take along time )
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl checkusers - show ONLY vulnerable and infected client end device
Clean INFECTED devices ( from previous check )
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl cleaninfected - show vulnerable and infected devices and REMOVE infection
More on Ubiquiti - security bug in changelog version 4.21, beta1.
UBIQUITI BUG
Detecting and removing

Reacting to the revealed vulnerability, we released ISPadmin, version 4.20, which included a utility for detecting and curing infected Ubiquiti units. Due to the emergency situation we released the very first version of the utility quickly.
Now we are presenting the utility with enhanced functionalities.
 Run the utility from ISPadmin console (connected via SSH) under root user, ISPadmin does not detect anything automatically!
Run the utility from ISPadmin console (connected via SSH) under root user, ISPadmin does not detect anything automatically!
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl
When running the utility without any parameter, help is displayed.
Check devices from ISP admin bookmark ROUTERS
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl check <username> <username2> <username3> <username4> <username5> - show ONLY vulnerable and infected ROUTERS ( AP )
Tests all Ubiquiti units inserted in . If you run this command, the system tries to attack the unit, and if it succeeds, the console displays information with IP address and firmware version. If the system succeeds in connecting to Ubiquiti unit, it tries to determine whether there is the virus or not. If yes, it displays such information in the console. Nothing else. When 10 units are tested, a dot appears on the screen to show you that the script is still running and testing other units.
Check devices like AP ....( may take a long time )
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl checkdevices <username> <username2> <username3> <username4> <username5>
- show ONLY vulnerable and infected devices ( Acces points )
Tests all devices inserted as “Device attached to device” in . In this case, the utility doesn´t care about device type since such information might not be available here. The utility tries to attack all IP addresses. If there are a lot of devices in your system, this might take a long time.
Check END USER devices ....( may take a long time )
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl checkusers <username> <username2> <username3> <username4> <username5>
- show ONLY vulnerable and infected client end device
Tests all IP addresses assigned to clients. The system tests all client-assigned IP addresses for it does not know whether a client has Ubiquiti device, or not. This operation might take a long time, since all IP addresses in the system are tested.
Clean INFECTED devices ( from previous check )
/usr/local/script/ispadmin/ubnt_vulnerability_test.pl cleaninfected
- show vulnerable and infected devices and REMOVE infection
If an infected unit is detected in the previous step, you may clean it this way. This operation connects to and cleans just those units, which are marked as infected. It means that prior to this step you have to run the utility with parameters check, checkdevices, or checkusers. Failing this no units are marked as infected and using parameter “cleaninfected” makes no difference.
A mandatory parameters are: check, checkdevices, checkusers, or cleaninfected. You may use user names, which you use for login to Ubiquiti units as an optional parameter. This is needed in cases when a key is stored in Ubiquiti unit after being attacked to enable login via ssh without password. You need to know the user name with which you connect to the system. If unknown, you won´t be able to connect. While running the vulnerability test, a default user name ubnt and user admin are tested. If you use neither of these, the script won´t be able to test vulnerability hence the need for entering a different username used for accessing the unit (no need for password). Then the system will try using these usernames.
Listing of UBNT units in ISPadmin
When you log into ISPadmin, you will see information about Vulnerability of UBNT devices:
In > Vulnerability of UBNT devices, you will find a tool for displaying vulnerable devices as detected by the utility - see above.
 Check the box at the end of each row (or check all, or you may use reversed selection) to select those devices, for which you want the system to update firmware - by clicking on on the bottom.
Check the box at the end of each row (or check all, or you may use reversed selection) to select those devices, for which you want the system to update firmware - by clicking on on the bottom.
NEWS
- A new filter Client group has been added to . You can use it for payment type Paired only.
- New system variables added:
- $CLI_RAW_NAME$ - the variable is replaced with client´s name from “Personal data” section.
- $CLI_NAME_INVOICING$ - the variable is replaced with client´s name from “Invoicing data” section.
- Bookmarks and have been amended with the following filters: “Invoice group”, “Client group”, “Client status”, and “Client payment type”.
- In scheduling overview - , and Client card / Scheduled interventions - an icon for editing the intervention is now displayed. This way you can edit any saved solution, even for completed tasks. One has to have “Edit” right for a given bookmark.
- Newly, you can turn off information about aggregation for Client portal. To do it, change ID ci_display_tariff_agregation in .
- You can now make a copy of a tariff in . There is an icon for it - - at the end of each row.
- When saving a client information, a new duplicity check on Company ID and personal ID is carried out. If a match is found, you´ll get information message. You will be able to save the record, anyway.
- You can now use http://ISPadmindomain.cz/new/www/find-client-by-phone-number/?number=420999888777 to get Client card of a client with the number used in “number” parameter. ISPadmin administrator must be logged in.
- You can now filter clients by Client groups if matched payments filter is used in .
- Information on Ram Disk (initialization, error messages, disk space) are now displayed in .
- You can now define your own report type in .
REWRITTEN PAGES
WIthdrawals
- New filters “Submission date”, “Invoice group” and “Locality” have been added to , and to Client card / Withdrawals. Columns with address, creation user and date, and time to withdrawal have been added. You can also add any number of notes to each withdrawal. There is the icon for it at the end of each row - . There are columns Last note date and Notes in the tab, too.
ADMINISTRATOR RIGHTS
- New rights to have been implemented. Previously, the rights were set for MasterAdmin, and for Main admin in some cases. Currently, the rights are automatically set for MasterAdmin only, and you have to set up the rest manually.
NEWS
- A new filter Client group has been added to . You can use it for payment type Paired only.
- New system variables added:
- $CLI_RAW_NAME$ - the variable is replaced with client´s name from “Personal data” section.
- $CLI_NAME_INVOICING$ - the variable is replaced with client´s name from “Invoicing data” section.
- Bookmarks and have been amended with the following filters: “Invoice group”, “Client group”, “Client status”, and “Client payment type”.
- In scheduling overview - , and Client card / Scheduled interventions - an icon for editing the intervention is now displayed. This way you can edit any saved solution, even for completed tasks. One has to have “Edit” right for a given bookmark.
- Newly, you can turn off information about aggregation for Client portal. To do it, change ID ci_display_tariff_agregation in .
- You can now make a copy of a tariff in . There is an icon for it - - at the end of each row.
- When saving a client information, a new duplicity check on Company ID and personal ID is carried out. If a match is found, you´ll get information message. You will be able to save the record, anyway.
- You can now use http://ISPadmindomain.cz/new/www/find-client-by-phone-number/?number=420999888777 to get Client card of a client with the number used in “number” parameter. ISPadmin administrator must be logged in.
- You can now filter clients by Client groups if matched payments filter is used in .
- Information on Ram Disk (initialization, error messages, disk space) are now displayed in .
- You can now define your own report type in .
REWRITTEN PAGES
WIthdrawals
- New filters “Submission date”, “Invoice group” and “Locality” have been added to , and to Client card / Withdrawals. Columns with address, creation user and date, and time to withdrawal have been added. You can also add any number of notes to each withdrawal. There is the icon for it at the end of each row - . There are columns Last note date and Notes in the tab, too.